Enable Remote Support Access
In order to enable remote support capability to a deployed UniFS-as-a-Service AWS install, an optional IAM Role can be deployed to the same AWS Account / Region as UaaS.
This IAM Role will grant very specific least-privilege, read-only access to the UaaS resources only to support engineers from Nasuni, and will only have access to the UaaS resources specifically, and no direct access to any file-system data.
Deploy Now
The required IAM role for remote support access can be deployed by another CloudFormation template. Use the form below to deploy this CloudFormation in your AWS Account. Review the installation steps below for a detailed list of all steps.

Deploy UaaS Support Role to AWS
Provide the same AWS Region and CloudFormation stack name used in your initial UaaS deploy.
Enabled Permissions
All permissions are scoped for the explicit resources created by the specified UaaS CloudFormation stack. All support role permissions are listed in the table below, but can also be inspected by downloading and viewing the source. These are all read-only permissions. No resources can be created, updated, or deleted with these permissions.
These support role permissions can only be assumed by qualified and approved Nasuni support engineers that have been granted access and have authenticated with multi-factor authentication.
| AWS Service | IAM Permissions | Resource Description |
|---|---|---|
| SQS | sqs:ReceiveMessagesqs:GetQueueAttributes |
Message queues for brokering work to UaaS workers |
| S3 | s3:GetObjects3:ListBucket |
Bucket containing inventory archive artifacts from UaaS jobs |
| DynamoDB | dynamodb:GetItemdynamodb:Querydynamodb:Scandynamodb:DescribeTable |
Database tables containing control data and metrics for UaaS in addition to UniFS metadata information |
| CloudWatch Logs | logs:Describe*logs:Get*logs:List*logs:StartQuerylogs:StopQuerylogs:TestMetricFilter |
Log entries from UaaS workers and API |
| Lambda Functions | lambda:Get*lambda:List* |
Compute resources for UaaS workers and API |
| CloudWatch Metrics | cloudwatch:GetDashboardcloudwatch:GetMetric* |
Various metrics from all UaaS resources collected into a CloudWatch dashboard |
| CloudFormation | cloudformation:List*cloudformation:Describe*cloudformation:Get* |
CloudFormation resources for the existing UaaS CloudFormation stack |
Installation Steps
-
Provide the same AWS Region and CloudFormation stack name used in your initial UaaS deploy. And click the "Deploy to AWS" button
-
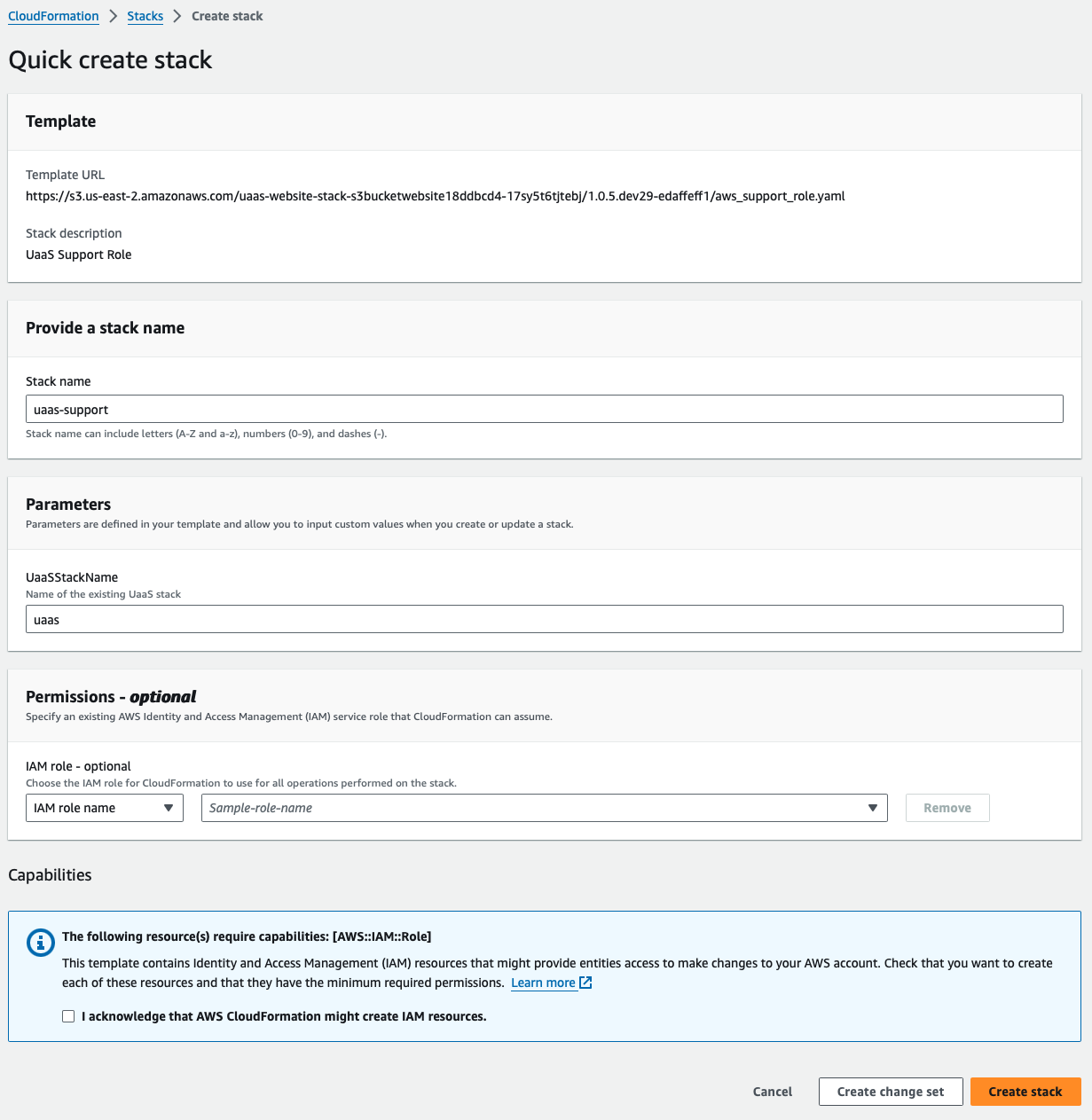
You'll be brought to the CloudFormation "Quick create stack" wizard.
-
The values for Stack name and UaaSStackName are pre-populated.
- The value Stack name can be customized to meet your needs
- The value for UaaSStackName must match the name of your existing UaaS stack for which you're enabling remote support access
-
(Optional) Select a custom IAM role to use for CloudFormation operations if desired. The deploy role used for the original UaaS deploy can also be used here. Otherwise, the identity performing the deploy of the support role must have permissions to create an IAM role.
-
Check the checkbox to acknowledge new IAM resources are being created.
-
Click Create stack button to start the provisioning of the new IAM support role.
-
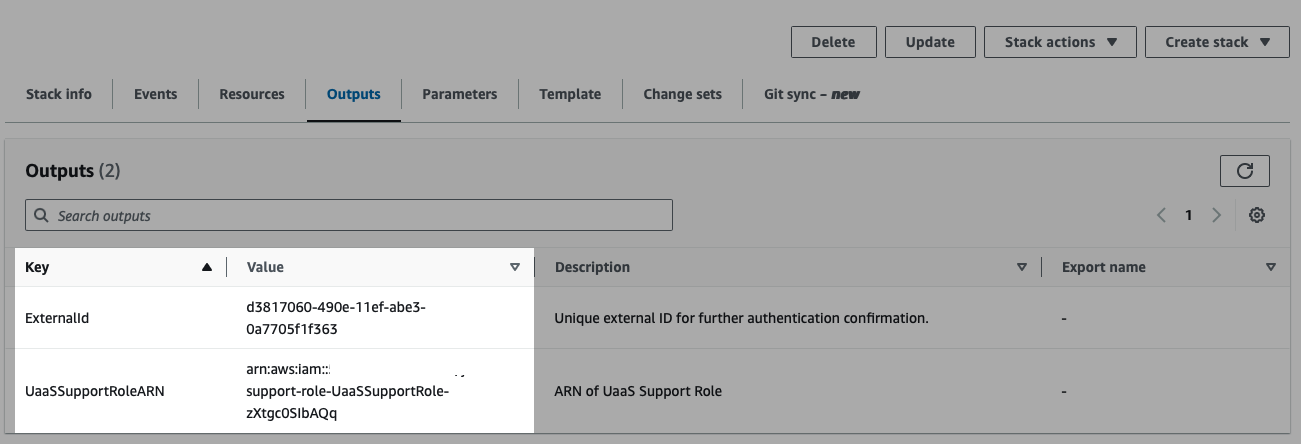
After stack has reached CREATE_COMPLETE status, go to the "Outputs" tab to retrieve the generated values of both ExternalId and UaaSSupportRoleARN.
-
Copy/Paste the generated values from the Outputs tab and transmit to Nasuni Support.
 UniFS™ as a Service
UniFS™ as a Service